Tag: Proactive Remediations
-
MSI Installer Error 1612: Missing MSI Local Cache
This is one of those articles that I actually hope nobody gets any use out of, because if you are getting use out of it, you’re not having a good day. This article is to cover the MSI Installer error 1612 and, more specifically, an Intune remediation I created to help understand the scope of…
-
Everything I Know on Subscription Activation
Overview: Over the past few years, I have had to write far too many blogs on or surrounding the topic of Subscription Activation. Fixed – Enterprise Subscription Activation Broken by KB5036893 & KB5036892Retired: Detecting & Automatically Removing Secondary “Work Or School” Accounts: Part 1Retired: Detecting & Automatically Removing Secondary “Work Or School” Accounts: Part 2Retired: Detecting & Automatically Removing…
-
Automating Reboot Maintenance Using Intune Proactive Remediations
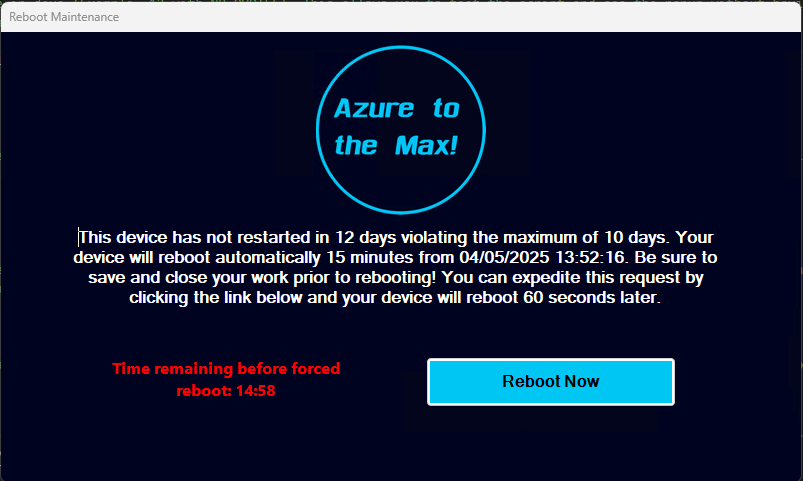
Intro: One of the age-old issues we in IT face is the employee who thinks rebooting their machine is a quarterly process, or at most a monthly process forced by Windows Updates. As we all know, lengthy up times have a tendency to create system instability and sluggishness, prevent application updates from processing (because much…
-
Automating Disk Space Alerts with Intune Proactive Remediations
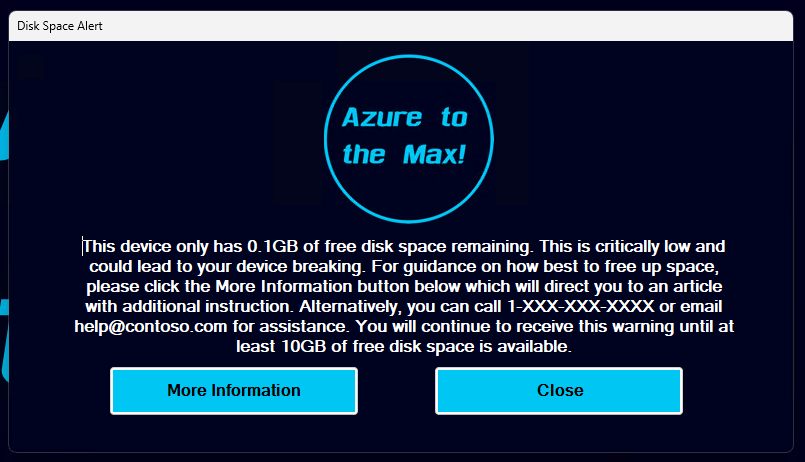
Intro: One of the age-old issues we in IT face is a machine running low on disk space. At best, this causes devices to become unstable, struggle to apply patches, and loose overall system (and employee) performance. At worst, it takes the device offline incurring downtime and potentially data loss. Thanks to ever-larger and cheaper…
-
Retired: Detecting & Automatically Removing Secondary “Work Or School” Accounts: Part 1
This Article Has Been Retired! Warning: I have chosen to “retire” this article. As time has marched on, and more information has been revealed, the blogs in this series have slowly become less and less up-to-date, and frankly, more and more of the information I was told as gospel has proved flawed or muddied. As…
-
Log Analytics for Application Usage Monitoring Part 1.6: Deploying the Script
Introduction: With your data ingesting and workbooks deployed, we are now ready to start deploying the collector via Proactive Remediations in Intune. This will likely be the final article in this series, at least for now. In this section, we will cover… Requirements: This should be pretty obvious, but you need to have completed the setup…
-
Log Analytics for Application Usage Monitoring Part 1.5: Importing the Workbook
Introduction: With your data now ingesting into Log Analytics, granted the collectors not yet deployed, we are ready to begin setting up our workbooks to further confirm data is coming in properly. Note: It would be a good idea to have at least a few devices manually ingest some data before starting this process. In this…
-
Log Analytics for Application Usage Monitoring Part 1.4: Sample Data, Tables, DCRs, Initial Ingestion
Introduction: We have now covered what this solution does and its cost, at least from an ingestion standpoint. Now, we will finally be deploying something! In this article, we will generate our sample data, use it to create our new tables and DCRs, grant the appropriate permissions on those DCRs, and perform an initial ingestion!…
-
Log Analytics for Application Usage Monitoring Part 1.3: Configure Event Auditing
As explained in prior articles, the Application Usage Monitoring makes use of Windows Event logs for data gathering. While the Event Log has a ton of useful information by default, the logs we need to capture for this tool to function are not logged by default and instead must be enabled via policy This article…
-
Log Analytics for Application Usage Monitoring Part 1.2: Cost
Introduction: Following my initial articles describing what is collected, how it is displayed, this article will cover the cost of this solution. Before we start, please know that I am no Azure cost “expert.” I can point you in the right direction and provide examples, but you need to consult with Microsoft and your internal…
